False Data Injection Attacks (FDIA) are a concrete and significant threat to industrial motion control systems, far from being merely hypothetical. These attacks involve manipulating critical data, often sensor feedback, to deceive the control system into misinterpreting the physical state of machinery, which can lead to severe consequences such as equipment damage, system instability, and dangerous uncontrolled movements posing risks to both production and personnel safety. Unlike simple disruptions, sophisticated FDIAs can be crafted to evade traditional anomaly detection by appearing consistent with expected system behavior, a capability starkly demonstrated by real-world malware like Stuxnet, which manipulated process data in Siemens PLCs to cause physical damage while hiding its actions. Consequently, the threat of FDIA is taken seriously by cybersecurity experts and industrial operators who recognize the vulnerabilities inherent in increasingly connected control systems and the potential for devastating physical impacts.
Recent advances in robust motion control have enhanced system resilience against non-malicious disturbances like unmodeled dynamics and measurement noise. However, the increasing connectivity in certain high-value industrial systems introduces potential vulnerability to False Data Injection Attacks (FDIAs). For specific application domains where the risk justifies the investment, research at the intersection of control theory and cybersecurity may help determine whether existing robust techniques require enhancement or if fundamentally new approaches are needed. This exploration should consider the practical constraints of real-time operation, computational limitations, and performance requirements while addressing the particular challenges posed by adversarial manipulations in networked motion control systems.
The research in cyberattack resilient motion control systems addresses critical vulnerabilities at the intersection of robotics and cybersecurity. The lab has pioneered several novel approaches to protect robotic systems from sophisticated attacks while maintaining operational performance.
Our research has identified a class of perfectly undetectable false data injection attacks (FDIAs) based on affine transformations that can compromise robotic manipulators and mobile robots. These attacks exploit weaknesses in the partially linear dynamic properties and symmetry of nonlinear robotic systems , allowing attackers to inject multiplicative and additive false data that remains hidden from detection. This work has been published in multiple papers including “Affine Transformation-based Perfectly Undetectable False Data Injection Attacks on Remote Manipulator Kinematic Control with Attack Detector” (Ueda and Blevins) in IEEE Robotics and Automation Letters.
To counter these vulnerabilities, the lab has developed encrypted control architectures using somewhat homomorphic encryption (SHE) techniques. Our approach encrypts the entire motion control scheme—including sensor signals, model parameters, and feedback gains—and performs computations directly on the encrypted data . This includes:
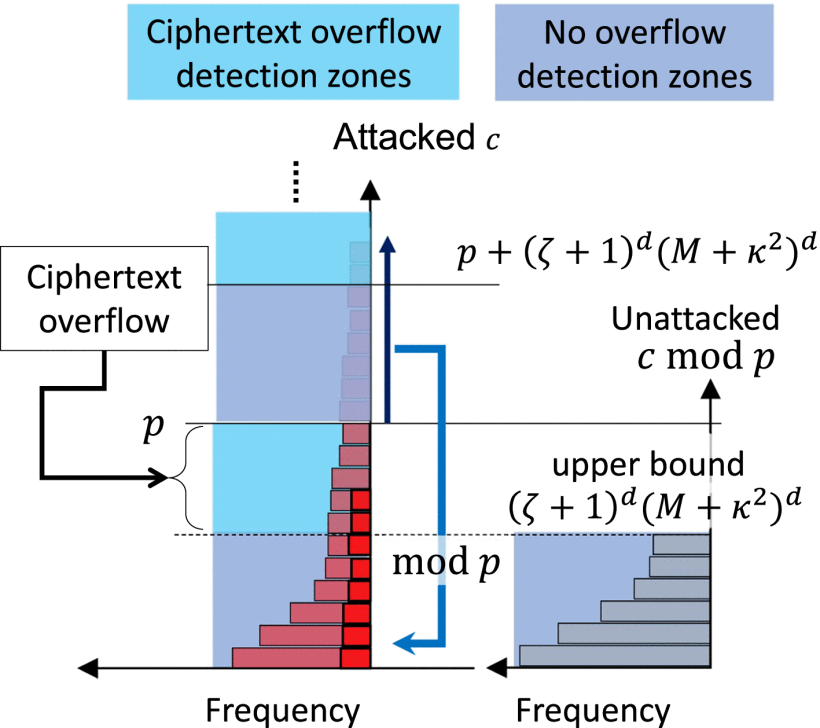
1) Encrypted model reference adaptive control with false data injection attack resilience via SHE-based overflow traps
2) Encrypted coordinate transformations for secure robotic teleoperation using parallelized SHE
3) Encrypted feedback linearization for nonlinear robot dynamics that preserves control performance while securing sensitive data
Our work applies geometric approaches and group theory to address the mathematical structure of system dynamics, particularly for nonlinear robotic systems. Current projects include research on “A Geometric Approach for Generalized Encrypted Control of Networked Dynamical Systems” funded by the NSF CMMI Program, which extends these security principles to broader networked control applications.
- Journal Papers
- Jun Ueda, Affine Transformation-based Perfectly Undetectable False Data Injection Attacks from Controller’s Perspective on State- and Output Feedback Linear Control Systems, IEEE Transactions on Industrial Cyber-Physical Systems, accepted, September 2025 (IEEE Xplore early access) (Code Ocean)
- Jun Ueda and Bin Kwon, Perfectly Undetectable Reflection and Scaling False Data Injection Attacks via Affine Transformation on Mobile Robot Trajectory Tracking Control, IEEE Transactions on Robotics, 10.1109/TRO.2025.3626620, 2025 [Arxiv] [IEEE Xplore early access]
- Hyukbin Kwon, Jacob Blevins and Jun Ueda, Defense Mechanisms Against Undetectable Cyberattacks on Telerobotic Systems, IEEE/ASME Transactions on Mechatronics, 2025 AIM Focused Section, June 18, 2025 [IEEE]
- Jacob Blevins and Jun Ueda, Encrypted Model Reference Adaptive Control with False Data Injection Attack Resilience via Somewhat Homomorphic Encryption-Based Overflow Trap, IEEE Transactions on Industrial Cyber-Physical Systems, March 2025 [SMARTech] [TechRxiv. DOI: 10.36227/techrxiv.172469519.92808714/v1], [Xplore]
- Jun Ueda, Jacob Blevins, Affine Transformation-based Perfectly Undetectable False Data Injection Attacks on Remote Manipulator Kinematic Control with Attack Detector, IEEE Robotics and Automation Letters, 8690 – 8697, Volume: 9, Issue: 10, DOI: 10.1109/LRA.2024.3451397, August 2024 [Arxiv] [IEEE Xplore]
- Conference Papers
- Hyukbin Kwon, Hiroaki Kawase, Heriberto Andres Nieves-Vazquez , Kiminao Kogiso, Jun Ueda, Perfectly Undetectable False Data Injection Attacks on Encrypted Bilateral Teleoperation System based on Dynamic Symmetry and Malleability, 2025 IEEE International Conference on Robotics and Automation (ICRA), accepted [Arxiv]
- Shane Kosieradzki, Saahas Yechuri, Jun Ueda, Encrypted Sensor and Actuator Interface for Encrypted Control Signals via Embedded Key Generation, the 2024 IEEE/SICE International Symposium on System Integration (SII 2024),
- Bin Kwon, Shane Kosieradzki, Jacob Blevins, Jun Ueda, Encrypted Coordinate Transformation via Parallelized Somewhat Homomorphic Encryption for Robotic Teleoperation, 2023 IEEE/ASME International Conference on Advanced Intelligent Mechatronics (AIM 2023), Seattle, WA, July 2023.
- Hiroaki Kawase, Waiman Meinhold, Jun Ueda, Encrypted Classification for Prevention of Adversarial Perturbation and Individual Identification in Health-Monitoring, 2023 IEEE/ASME International Conference on Advanced Intelligent Mechatronics (AIM 2023), Seattle, WA, July 2023.
- Xiaofeng Zhao, Shane Kosieradzki, Jun Ueda, Distributed Simulation of Encrypted Dynamics via Functional Mockup Units, 2023 IEEE/SICE International Symposium on System Integrations (SII 2023)
- Shane Kosieradzki, Xiaofeng Zhao, Hiroaki Kawase, Kiminao Kogiso, Jun Ueda, Secure Teleoperation Control Using Somewhat Homomorphic Encryption, IFAC 2022 Modeling, Estimation, and Control Conference (MECC 2022),October 2022 [LINK]
- Shane Kosieradzki, Yingxin Qiu, Kiminao Kogiso, Jun Ueda, Rewrite Rules for Automated Depth Reduction of Encrypted Control Expressions with Somewhat Homomorphic Encryption, Proceedings of the 2022 IEEE/ASME International Conference onAdvanced Intelligent Mechatronics (AIM 2022) , pp. 804-809, July 2022. [LINK]

NSF CMMI Grant Number 2112793 and FRR 2516189
