Ueda is awarded an endowed professorship.
Dr. Jun Ueda has been awarded Harris Saunders Jr. Professorship at the School of Mechanical Engineering.
Paper on perfectly undetectable attack on mobile robot dynamics and attack detection using state monitoring function published in Transactions on Robotics
Perfectly Undetectable Reflection and Scaling False Data Injection Attacks via Affine Transformation on Mobile Robot Trajectory Tracking Control, 10.1109/TRO.2025.3626620, IEEE Transactions on Robotics, https://ieeexplore.ieee.org/document/11219216Jun Ueda and Hyukbin Kwon With the increasing integration of cyber-physical systems (CPS) into critical applications, ensuring their resilience against cyberattacks is paramount. A particularly concerning threat…
Paper on Affine Transformation-based Perfectly Undetectable False Data Injection Attacks published in IEEE Trans. Industrial Cyber-Physical Systems
https://ieeexplore.ieee.org/document/11183579 J. Ueda, “Affine Transformation-based Perfectly Undetectable False Data Injection Attacks from Controller’s Perspective on State- and Output Feedback Linear Control Systems,” in IEEE Transactions on Industrial Cyber-Physical Systems, doi: 10.1109/TICPS.2025.3615175 This paper demonstrates the fundamental vulnerability of networked linear control systems to perfectly undetectable false data injection attacks (FDIAs)…
Cybersecurity for the Physical World
Jun Ueda receives NSF grant to research a critical gap in networked robotic systems https://cos.gatech.edu/news/cybersecurity-physical-world
Yingxin’s paper has been published in IEEE T-MRB
Yingxin Qiu, Mengnan Wu, Lena Ting, and Jun Ueda, Two-Stage Optimized Perturbation Design for Efficient Human Arm Impedance Identification with Device Dynamics Compensation, IEEE Transactions on Medical Robotics and Bionics. System identification of human sensorimotor systems requires multiple experimental trials to achieve reliable parameter estimates, yet practical constraints limit the…
New NSF award for research on cybersecurity in motion control systems
NSF Foundational Research in Robotics (FRR), Geometric Vulnerabilities in Networked Robotic Systems: Analysis of Affine Transformation-Based False Data Injection Attacks and Their Countermeasures (#2516189), PI: Ueda, $691,375, 09/01/2025-08/31/2028 This research develops a comprehensive theoretical framework using Lie group theory and differential geometry to characterize geometric vulnerabilities in networked robotic systems…
Dr. Jun Ueda Named ASME Fellow
This recognition from the American Society of Mechanical Engineers (ASME) highlights his dedicated work in the field.
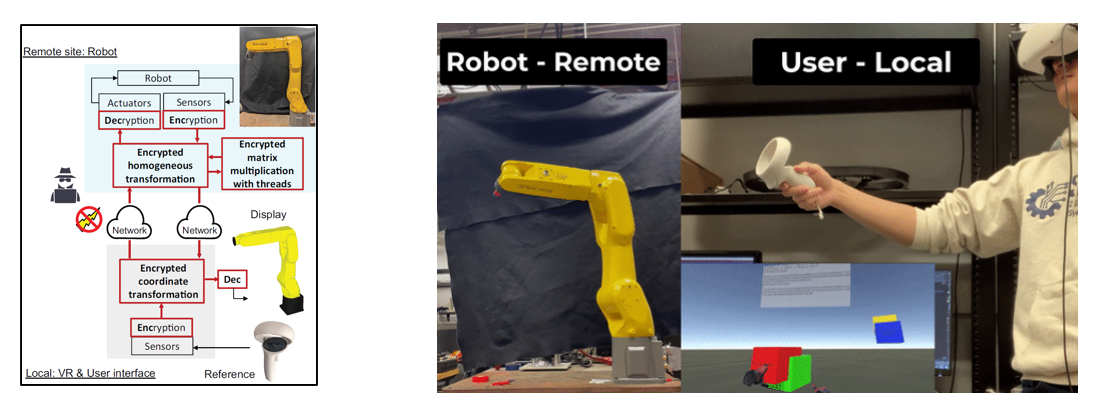
IEEE TMECH Defense Mechanisms Against Undetectable Cyberattacks on Encrypted Telerobotic Control Systems
A paper on defense mechanisms against false data injection attacks utilizing malleability of homomorphic encryption has been published in IEEE TMECH. H. Kwon, J. Blevins and J. Ueda, “Defense Mechanisms Against Undetectable Cyberattacks on Encrypted TeleroboticControl Systems,” in IEEE/ASME Transactions on Mechatronics, doi: 10.1109/TMECH.2025.3570933. Abstract: Networked control systems are vulnerable…